2023.05.15 - [네트워크 수업/Docker] - zfw.pdf 23.05.15

IP Address
[FW]
int f0/1
no shut
ip add 1.1.100.5 255.255.255.252
int f0/0
no shut
ip add 200.1.2.254 255.255.255.0
int f2/0
no shut
ip add 200.1.1.254 255.255.255.0
int f1/0
no shut
ip add 1.1.100.1 255.255.255.252
do show ip route
[CE]
int f0/0
no shut
ip add 1.1.100.2 255.255.255.252
int f1/0
no shut
ip add 2.2.2.254 255.255.255.0
int f0/1
shut
mac-address 1234.1234.1122
no shut
ip add dhcp
[DMZ]
int f0/1
no shut
ip add 100.1.1.254 255.255.255.0
int f0/0
no shut
ip add 1.1.100.6 255.255.255.252
zone 이 나눠짐(DMZ inside, outside 처럼)
zone이 형성되면 traffic이 아무것도 오갈수가 없다.
일반 방화벽처럼 구현됨
일반 라우터로 구현될수 있는 방화벽과 유사한 것을 zone based fire이라고 한다.
Routing
[FW]
ip route 100.1.1.0 255.255.255.0 f0/1 1.1.100.6
ip route 0.0.0.0 0.0.0.0 f1/0 1.1.100.2
[DMZ]
ip route 0.0.0.0 0.0.0.0 f0/0 1.1.100.5
[CE]
ip route 1.1.100.4 255.255.255.252 f0/0 1.1.100.1
ip route 100.1.1.0 255.255.255.0 f0/0 1.1.100.1
ip route 200.1.1.0 255.255.255.0 f0/0 1.1.100.1
ip route 200.1.2.0 255.255.255.0 f0/0 1.1.100.1
ip route 0.0.0.0 0.0.0.0 f0/1 10.0.0.1
NAT
[CE]
ip access-list standard INGRESS
permit 100.1.1.0 0.0.0.255
permit 200.1.1.0 0.0.0.255
permit 200.1.2.0 0.0.0.255
permit 2.2.2.0 0.0.0.255
ip nat inside source list INGRESS interface f0/1 overload
int range f1/0 , f0/0
ip nat inside
int range f0/1
ip nat outside



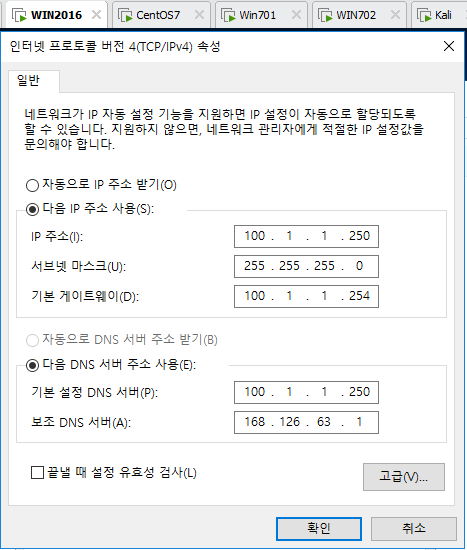

KALI
vi /etc/network/interfaces
인터넷으로 핑날아가는지 확인
방화벽
[FW]
zone security Inside
exit
zone security DMZ
exit
zone security Outside
exit
//firewall 이 어느 zone에 들어가있는지 알려준다.
int range f0/0 , f2/0
zone-member security Inside
int f1/0
zone-member security Outside
int f0/1
zone-member security DMZ
show zone security //확인 명령어

//이렇게 나뉘면 이제 zone간에 통신이 안된다.
//같은 zone에서만 ping 가능.
//고가의 router에만 이런 설정 가능. 중저가는 xx

DNS,HTTP, HTTPs, SMTP, POP3, IMAP, FTP
[FW]
access-list 100 permit ip any any
class-map type inspect IN->OUT_C
match access-group 100
exit
policy-map type inspect IN->OUT_P
class type inspect IN->OUT_C
inspect // 모든것 허용해주는 명령
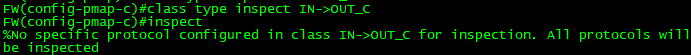
//Name of zone-pair 의 이름은 interface 와 달라도 되지만 웬만하면 같게 맞춰줘라.
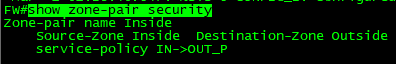
zone-pair security Inside source Inside destination Outside
service-policy type inspect IN->OUT_P //모든 것 다 허용할거다
FW#show zone-pair security
FW#show policy-map type inspect zone-pair sessions
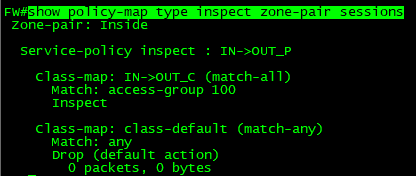
FW(config)#class-map type inspect match-any WEB //match-any(or 연산)를 생략하면 match-all 이 기본값이 된다(and연산)
FW(config-cmap)#match protocol http
FW(config-cmap)#match protocol https
//http 또는 https //or 연산
access-list 101 permit ip any host 100.1.1.251
access-list 102 permit ip any host 100.1.1.250 //web traffic 분류
//web server 와 dns server 분류
class-map type inspect WEB_SER //and 연산 --class map에서 다른 class map을 호출했다!!(acl도 호출 가능) --and연산하고 싶어서 끌고온것.
match access-group 101 //출발지가 어디든간에 목적지가 101( 100.1.1.251) 로 가는것
match class-map WEB
class-map type inspect DNS_SER
match access-group 102
match protocol dns
//Mail 서버 분류
class-map type inspect match-any MAIL_SERVICE//smtp pop imap이 and 연산되면 안되니까 match-any 넣기
match protocol smtp
match protocol pop3
match protocol imap
class-map type inspect FTP_C
match protocol ftp
exit
//이제 policy
policy-map type inspect IN->DMZ_P
class type inspect WEB_SER
inspect //이 class map을 검사하고 검증해라
exit
class type inspect DNS_SER
inspect
class type inspect MAIL_SERVICE
inspect
class type inspect FTP_C
inspect
//zone-pair
zone-pair security IN->DMZ source Inside destination DMZ
service-policy type inspect IN->DMZ_P
do show policy-map type inspect IN->DMZ_P

//여기까지 4개 허용(web, dns, ftp, mail)
DMZ → Outside //DNZ,SMTP
# show class-map type inspect DNS_SER
Class Map type inspect match-all DNS_SER (id 4)
Match access-group 102
Match protocol dns
class-map type inspect DNS_C
match protocol dns // protocol 이 dns 면서 100.1.1.250으로 가는 것(용도가 다르다)
exit
class-map type inspect SMTP_C
match protocol smtp
exit
//policy
policy-map type inspect DMZ->OUT_P
class type inspect DNS_C
inspect
exit
class type inspect SMTP_C
inspect
exit
//zone-pair
zone-pair security DMZ->OUT source DMZ destination Outside //출발지는 DMZ, 목적지는 Outside
service-policy type inspect DMZ->OUT_P
Outside → DMZ // DNS, HTTP, HTTPs,SMTP,FTP
policy-map type inspect OUT->DMZ_P
class type inspect WEB_SER
inspect
class type inspect DNS_SER
inspect
class type inspect FTP_C
inspect
class type inspect SMTP_C
inspect
zone-pair security OUT->DMZ source Outside destination DMZ
service-policy type inspect OUT->DMZ_P
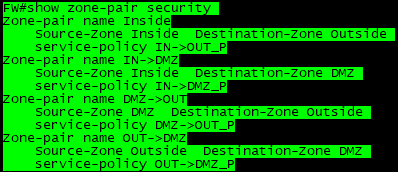
# show zone-pair security
[root@Docker1 ~]# ifconfig
inet 100.1.1.251 //ip확인
[root@Docker1 ~]# systemctl start httpd
[root@Docker1 ~]# systemctl restart httpd
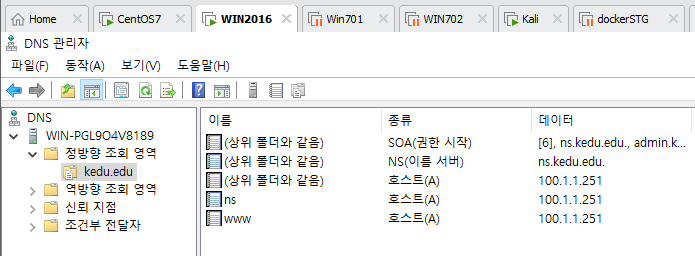
Win701에서 이름쓰기 되나 확인 --> 난 안됨;;;;
nslookup
www.kedu.edu
[FW] show run
class-map type inspect match-all SMTP_C
match protocol smtp
class-map type inspect match-any MAIL_SERVICE
match protocol smtp
match protocol pop3
match protocol imap
class-map type inspect match-all DNS_SER
match access-group 102
match protocol dns
class-map type inspect match-all DNS_C
match protocol dns
class-map type inspect match-all IN->OUT_C
match access-group 100
class-map type inspect match-any WEB
match protocol http
match protocol https
class-map type inspect match-all WEB_SER
match access-group 101
match class-map WEB
class-map type inspect match-all FTP_C
match protocol ftp
!
!
policy-map type inspect DMZ->OUT_P
class type inspect DNS_C
inspect
class type inspect SMTP_C
inspect
class class-default
policy-map type inspect OUT->DMZ_P
class type inspect WEB_SER
inspect
class type inspect DNS_SER
inspect
class type inspect FTP_C
inspect
class type inspect SMTP_C
inspect
class class-default
policy-map type inspect IN->DMZ_P
class type inspect WEB_SER
inspect
class type inspect DNS_SER
inspect
class type inspect MAIL_SERVICE
inspect
class type inspect FTP_C
inspect
class class-default
policy-map type inspect IN->OUT_P
class type inspect IN->OUT_C
inspect
class class-default
!
zone security Inside
zone security DMZ
zone security Outside
zone-pair security Inside source Inside destination Outside
service-policy type inspect IN->OUT_P
zone-pair security IN->DMZ source Inside destination DMZ
service-policy type inspect IN->DMZ_P
zone-pair security DMZ->OUT source DMZ destination Outside
service-policy type inspect DMZ->OUT_P
zone-pair security OUT->DMZ source Outside destination DMZ
service-policy type inspect OUT->DMZ_P
!
!
!
!
interface FastEthernet0/0
ip address 200.1.2.254 255.255.255.0
zone-member security Inside
duplex auto
speed auto
!
interface FastEthernet0/1
ip address 1.1.100.5 255.255.255.252
zone-member security DMZ
duplex auto
speed auto
!
interface FastEthernet1/0
ip address 1.1.100.1 255.255.255.252
zone-member security Outside
duplex auto
speed auto
!
interface FastEthernet2/0
ip address 200.1.1.254 255.255.255.0
zone-member security Inside
duplex auto
speed auto
!
ip http server
no ip http secure-server
ip forward-protocol nd
ip route 0.0.0.0 0.0.0.0 FastEthernet1/0 1.1.100.2
ip route 100.1.1.0 255.255.255.0 FastEthernet0/1 1.1.100.6
!
!
!
access-list 100 permit ip any any
access-list 101 permit ip any host 100.1.1.251
access-list 102 permit ip any host 100.1.1.250
!
!
!
!
control-plane
!
!
!
!
!
!
!
!
!
line con 0
exec-timeout 0 0
logging synchronous
line aux 0
line vty 0 4
!
!
end
'네트워크 수업 > Docker' 카테고리의 다른 글
| Docker Image (0) | 2023.05.18 |
|---|---|
| 도커네트워크 23.05.16 (0) | 2023.05.16 |
| Docker - NSF 서버구축 23.05.12 (0) | 2023.05.12 |
| 클라우드서버 구축 nextcoud 23.05.11 (0) | 2023.05.11 |
| CLI(Command-line Interface) 23.05.11 (0) | 2023.05.11 |




댓글